Apdu Commands Create File
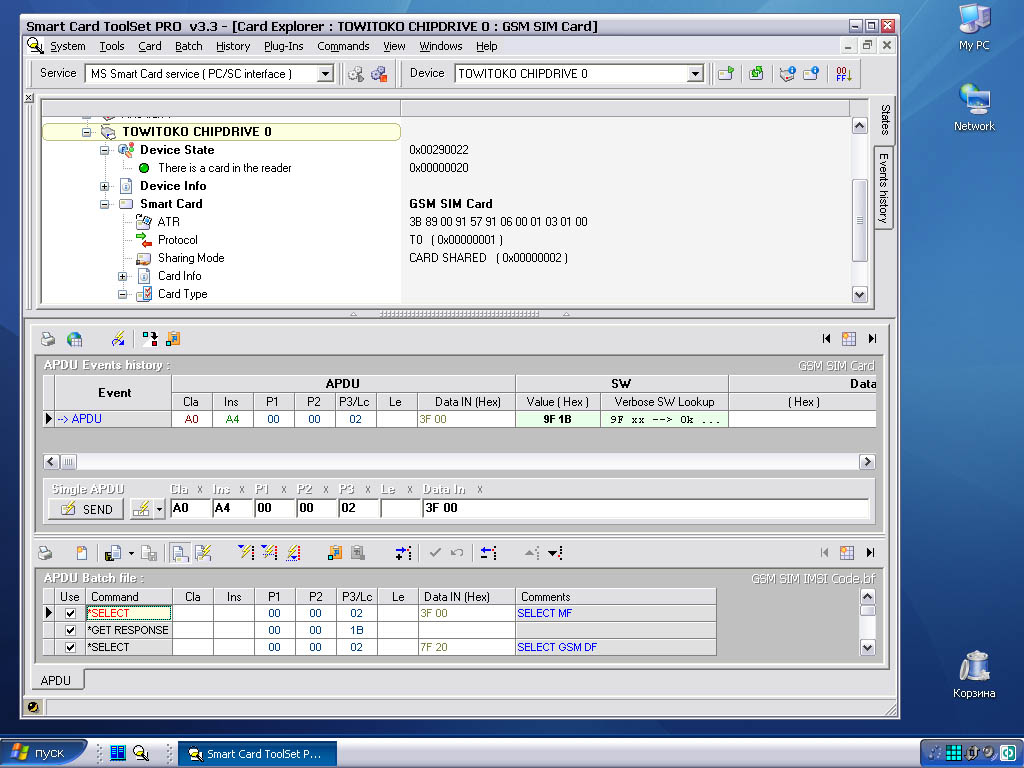
Smart Cards Active. X control download page. What kind of smart cards and the card readers are supported by the SCard. X Easy SCard. X Easy Active. X control is based on the MS Smart Card Service which implements the PCSC Specifications 1. It means that you can successfully use any of PCSC compatible devices. USB tokens e. t. c., and you can work with any of ISO 7. I dont know what the organization hierarchy is. As for your question those standards explain the format of the data structures of each file type on the filesystem. Clarence Clemons Hero more. In the context of smart cards, an application protocol data unit APDU is the communication unit between a smart card reader and a smart card. The structure of the. The Language of BACnetObjects, Properties and Services By Bill Swan, Alerton Technologies, Inc. BACnet Building Automation and Control Network is the open data. CreateFileGood.png' alt='Apdu Commands Create File' title='Apdu Commands Create File' />GSM SIM cards, EMV payment cards, identity. To be able to work with contactcontactless memory cards you need to use the specific card reader which allows you to encapsulate the specific memory card commands readwriteverify e. APDUs. In other words you need the card reader which allows you to work with a memory card in the way you use for contact smart cards. For example to use our software with memory cards you can use one of the following card readers ProxNRoll PCSC, OMNIKEY 5. Priore-SmartCard-ActiveX-1.4.jpg' alt='Apdu Commands Create File' title='Apdu Commands Create File' />
 Bulletin SB17079 Vulnerability Summary for the Week of March 13, 2017 Original release date March 20, 2017. ISOIEC 7816 is an international standard related to electronic identification cards with contacts, especially smart cards, managed jointly by the International. FJi3BCr0F6QEUyc0J_YsWbY3gljWbzkVbk121BlNasQ8cJ0lFbWUzA8ZPWuBMnO789Qz' alt='Apdu Commands Create File' title='Apdu Commands Create File' />Technical AnalysisCrashOverride malware represents a scalable, capable platform. The modules and capabilities publically reported appear to focus on organizations. What is the Security Tango The Security Tango is my name for the dance you have to do every time you want to assure yourself that your computer is free of viruses.
Bulletin SB17079 Vulnerability Summary for the Week of March 13, 2017 Original release date March 20, 2017. ISOIEC 7816 is an international standard related to electronic identification cards with contacts, especially smart cards, managed jointly by the International. FJi3BCr0F6QEUyc0J_YsWbY3gljWbzkVbk121BlNasQ8cJ0lFbWUzA8ZPWuBMnO789Qz' alt='Apdu Commands Create File' title='Apdu Commands Create File' />Technical AnalysisCrashOverride malware represents a scalable, capable platform. The modules and capabilities publically reported appear to focus on organizations. What is the Security Tango The Security Tango is my name for the dance you have to do every time you want to assure yourself that your computer is free of viruses.